
For many years, virtual data rooms (VDRs) have been the standard for sharing confidential documents on a secure online platform. Traditional data rooms and VDRs allow sellers or intermediaries to share information with third parties such as potential investors, acquirers, and partners. VDRs are often used during mergers and acquisitions (M&A) transactions, as they provide a secure and efficient way for buyers to review the target company's financial records, intellectual property, and other sensitive information.
Virtual data rooms can also protect intellectual property and proprietary/confidential business information, including valuable trade secrets. These trade secrets include financial statements, software code, conceptual or system product designs, formulas, recipes, manufacturing processes, customer lists, and marketing plans. This data can be shared for a variety of non-transactional purposes.
As technology advances, so do the methods used by cybercriminals (i.e., APTs) and rogue nation-states to gain access to sensitive information, such as intellectual property and trade secrets[1]. A single layer of encryption is no longer enough to keep your data safe. Intellectual property is often the most valuable asset of a technology company. It can take years of research and development to create new intellectual property, which can be worth millions or even billions of dollars. APTs increasingly target intellectual property[2], which they know can be used for ransom or resold on dark web marketplaces like Russian Market, Genesis, and BrianCC.
Most VDRs use old encryption methods such as RSA, Diffie Hellman key exchanges, and Elliptic Curve Cryptography, which are vulnerable to quantum computer attacks[3] and an emerging attack strategy: "steal now, decrypt later"[4] when quantum computers can break these methods much faster than traditional computers, so using these older encryption algorithms to store sensitive data is a major security risk.
Polynom deploys the latest NIST-approved post-quantum cryptography (PQC) algorithms, a new generation of encryption algorithms designed to resist quantum computer attacks. In addition, Polynom enables VDR users to utilize our double encryption innovation, Social Encryption™ ("SE"), as an extra measure of PQC security.
Polynom's Social Encryption™ is a quantum-resistant technology that allows users to communicate E2EE across a network without manually exchanging keys. It does this by replacing network key exchanges with a symmetric key exchange from already known sources of entropy that can be acquired from anything, including passphrases, contents of files/images, or any offline/online source of data. By using shared experiences and knowledge, there is no need to perform traditional network handshakes to exchange shared keys.
Social Encryption is a "rolling cipher" algorithm, meaning that each entropy line is derived from a separate source and is compounded into the final result, an AES 256 shared key. This final AES 256-bit key is used for E2EE encrypting all content between parties using AES 256-bit GCM mode. SE keys are identified across the network using an SHA-512 hash derived from an HMAC (hash-based message authentication code). This allows parties involved to know which SE key to use for the decryption of content without revealing any of the entropic data and/or other secrets used to derive the SE keys.
There are several steps that companies can take to protect their trade secrets in Polynom VDRs.
These include:
- Password protecting the applicable folders and VDRs by limiting access to authorized users with shared Social Encryption keys. Whitelisting—allowing only individuals with a legitimate need to access the VDR should be granted access. Authorized users receiving Social Encryption keys and any user receiving access to trade secret folders should sign non-disclosure agreements (NDAs) specifically referencing the "CONFIDENTIAL" or TRADE SECRET" documents.
- Additional layers of entropy using Social Encryption passwords and limiting file/folder access to the most sensitive documents.
- Labeling all trade secret documents. All documents that contain trade secrets should be clearly labeled as such. This can be done by adding "TRADE SECRET" and "CONFIDENTIAL" to the filename or by watermarking the document.
- Monitoring and logging access to VDR rooms through Polynom access privilege settings (via Polynom Server).
- Users can restrict individual authorized users by their Graphatar identity to ensure that only access is granted to specific cryptographic identities.
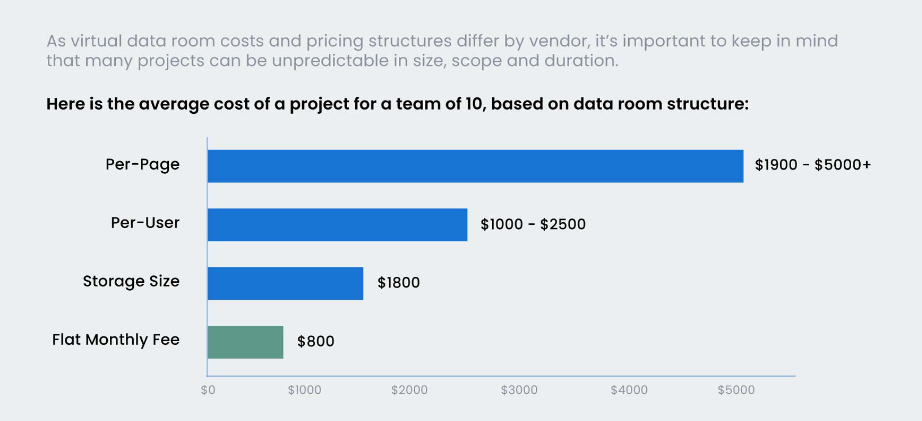
Polynom is more affordable than VDRs. Polynom is a free-to-pay-as-you-go service that only pays for your storage system. There are no Polynom setup fees or monthly charges for our Community-level edition. Users are responsible for their server infrastructure. Polynom Community users can save significant money, especially if they only need to share documents occasionally. Polynom Enterprise users can expect modest license fees if the user base is an SME.
To set up a Polynom VDR, please follow the succeeding steps and access the Polynom wiki for step-by-step guidance:
Utilizing Polynom Community Edition is free and easy. First, download the Polynom Community client for your operating system at https://polynom.app/. Then install and follow the wizard to carefully select your Graphatar (it may take time to select your likeness). The Graphatar is your cryptographic identity and is cryptographically impossible to copy. Make sure to back up your Graphatar identity. Then, join a Polynom server.
You must install the Polynom Community Edition server to create a free collaborative community. Let's start with the basic steps. You'll need any x86 or AMD64-equivalent PC or mini PC-equivalent (e.g., Intel NUC, ASUS PN 64, etc.) to run Linux. Download the Polynom Linux server. Then, follow the instructions from the Polynom.wiki site. You can run your collaborative server in minutes with NIST Security Level V (the highest available) and protect your data with future-proof post-quantum cryptography.
Polynom is both an on-premise/self-hosted and virtual cloud-based platform, so you can access and provide access to sensitive documents from anywhere with an internet connection.
Polynom is an additional security feature (i.e., Quantum Rooms™) that allows users to set up self-destructing rooms for ultimate confidential sharing in maximum privacy; you can set expiration dates for your documents to automatically be deleted after a certain period.
If you are looking for a secure and affordable way to share documents, Polynom is a great option.